Healthcare Cybersecurity Top Threats & Industry Trends in 2023
Industry Trend Comparison
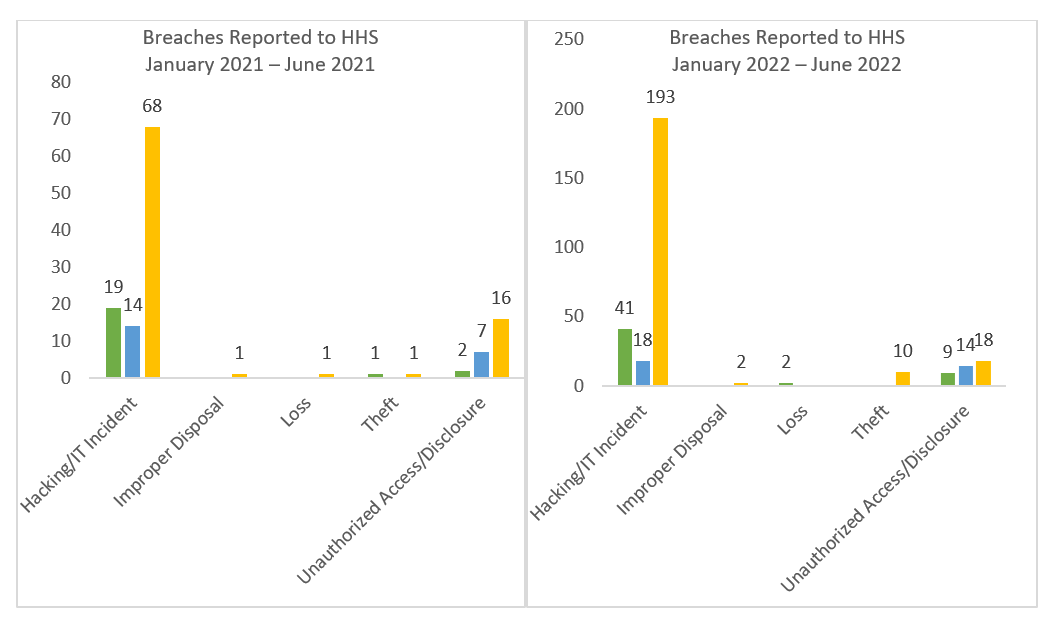
The Department of Health and Human Services (HHS) has reported an 84% increase in the number of data breaches against health care organizations from 2018-2021, highlighting the growing concern of cybersecurity threats in healthcare. Data reported through the first half of the year is consistent with the rate of increase reported each year.
Top 3 Cybersecurity Threats in Healthcare
- Basic Web Application Attacks (BWAA)
Web applications are ideal targets for adversaries – they are intentionally exposed publicly, are always available, and can be a door to a database containing potentially sensitive information. Also known as application-layer attacks, these exploits take advantage of web services that are designed to receive requests and provide responses. When not properly secured, web applications may divulge information to an attacker in response to requests or through manipulation of the application’s logic. The seven most common types of web application attacks are:
- Cross-site scripting (XSS)
- SQL injection (SQLi)
- Path traversal
- Local file inclusion
- DDoS attacks
- Cross-site request forgery (CSRF)
- XML external entity (XXE)
Source: HHS.Gov
The healthcare sector has seen the greatest increase in BWAAs relative to other industries, and web applications are to mission-critical to achieving the goals of HealthEdge. A layered defense strategy must be used to protect applications. HealthEdge employs a variety of protective and defensive measures that work together and complement one another to reduce possible opportunities for exploitation.
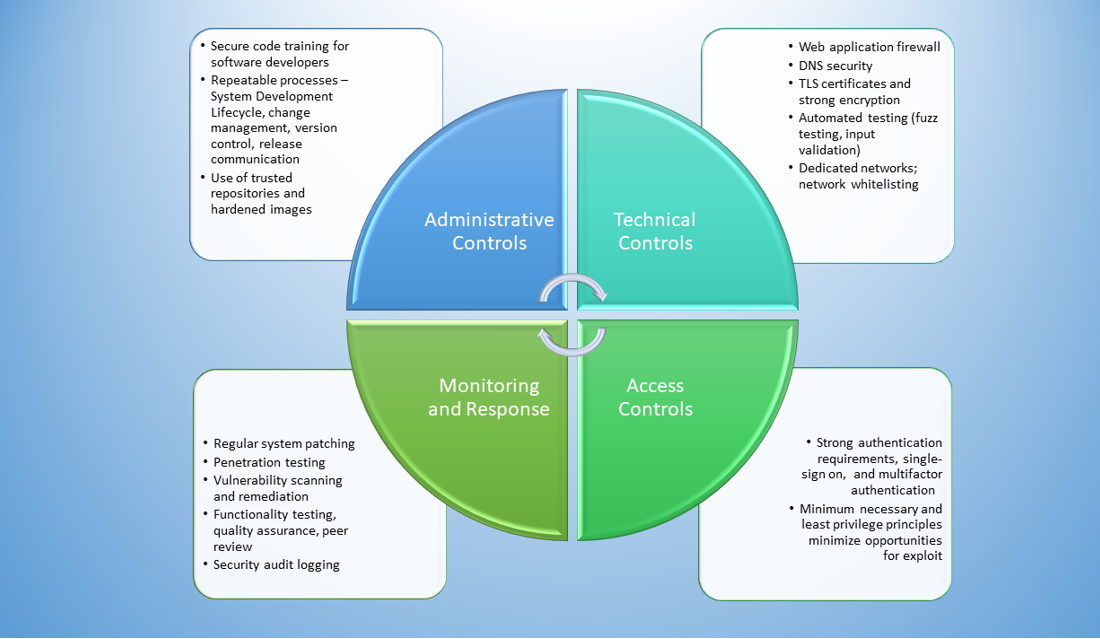
- System and Network
Zero-day attacks take advantage of previously unknown vulnerabilities that, as a result, have no known patch available. The vulnerability is discovered by the security community at the same time that its exploit becomes known. Because no time exists between the discovery of the vulnerability and the patch, these exploits are collectively referred to as “zero-day vulnerabilities,” “zero-day exploits,” or simply “zero-days”. Because code and vulnerability scanners, security posture management tools, and behavior monitoring technologies rely on previously identified vulnerabilities and exploits, these normally useful tools are less effective as a means of prevention or detection of zero days. Instead, security teams strive to prevent large-scale damage and minimize collateral damage in the event that the initial defenses fail.
While there is no silver bullet to preventing zero-day attacks, the opportunities for exploit can be reduced through multiple controls and best practices:
- Data and network isolation – Prevent lateral movement such that if a single system is compromised, the damage or access is limited to that system.
- Penetration testing and bug bounty – Also known as security researchers, penetration testers or bug bounty-hunters are software engineers that get paid to intentionally attempt to exploit systems in any way to potentially find their own zero days and the bad guys to the punch.
- Patching deployment planning – Once zero days have been discovered “in the wild,” it is of critical importance that the patch is received, applied, tested, and deployed to the production environment. This requires internal technology teams to be at the ready and know their role to patch the system as soon as possible.
- Monitoring and alerting – This continuous effort is important in identifying strange activities and responding to events that are validated as security incidents. This is commonly achieved through firewalls that inspect the network’s traffic, access control monitoring, audit logging, and automation capability to detect and notify anomalous activities to stop malicious actors in their tracks.
- Insider Threats
Another common threat that is central to the focus of security teams is the insider threat. An insider can be anyone who has authorized network, system, or application access, be it an employee, a third-party contractor, or business partner.
An insider threat does not imply that the insider is malicious, nor do insider threats require malicious or disgruntled actors at all. Instead, anyone who uses their authorized access, wittingly or unwittingly, to harm to the organization falls into this category. Threats include espionage, unauthorized viewing, modifying, disclosure of information, theft, loss, or unacceptable use of organizational resources or capabilities. Administrative and technical controls must be implemented for all possibilities to mitigate risk.
- Annual training is just as important as regularly informing all users about current phishing campaigns, cybersecurity trends, and other current events. Strong organizational security threat awareness ensures each of us are aware of our responsibilities as the first layer of defense.
- Least privilege and minimum necessary principles ensure that a user account cannot gain access to information beyond the scope of the user’s job requirements, even if that account were compromised. This limits the total damage that can be done by any single individual.
- Access controls and regular validation of provisioned access ensures users are appropriately provisioned for their role and that access creep is minimized. Access controls requiring strong passwords and multifactor authentication help prevent account takeovers.
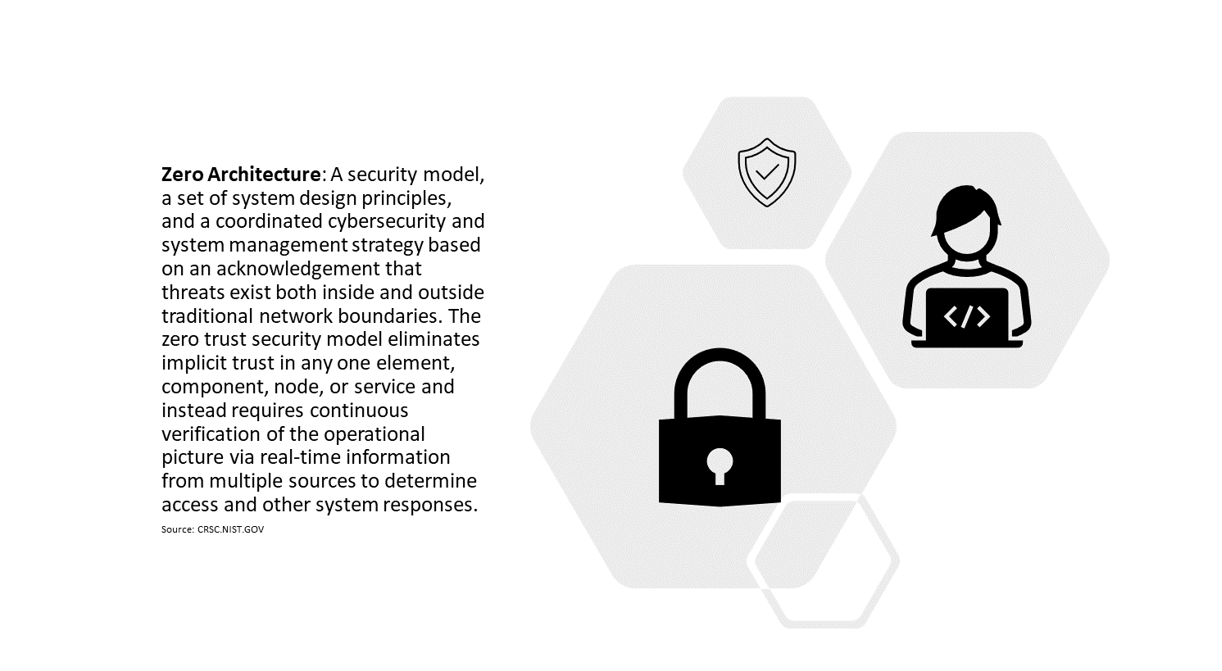
- Zero-trust architecture is a relatively new security concept with a slogan of “never trust, always verify.” The core belief of zero trust is that no user, system, network, or service operating outside or even within the security perimeter is implicitly trusted, even if they previously authenticate. In simpler terms, acquiring legitimate access to one system or network should never automatically confer access to another without additional validation. This security model limits damage that can be done if a single security control fails at any location within an organization’s ecosystem.
HealthEdge & Cybersecurity
HealthEdge understands what it means to be a good steward of customer data and we take this responsibility seriously. Our teams work around the clock to ensure maturity when it comes to pillars of security. Follow us next month when we dive further into cybersecurity threats in healthcare.
